We hear about hacking in the news all the time. Equifax, Home Depot, Target, Uber, Twitter and more. If you think your small or medium-sized business isn’t a large enough target, you’re wrong. SMBs are the fastest-growing hacking sector today. This is because criminals can typically break into your business technology within a matter of minutes. The pay-off may be smaller, but it doesn’t require much effort on their part.
For years, the average small business in the U.S. was an unlikely target for a sophisticated cyberattack. Fewer financial resources and a relatively unknown brand worked in your favor to ward them off. This is no longer the case.
In 2005, an official study by the State of Utah revealed that:
Although this data is old, it’s still relevant today.
In 2017, the Sans Institute published a study on cybersecurity spending that revealed the average company that takes IT security seriously takes 5 to 10% of their annual revenue and applies it to IT protection. The financial sector is spending from 12% to 15% on cybersecurity protection.
There are very real risks to our businesses. And the reality is that we must take action to protect our technology and digital information. If you don’t, your business is vulnerable like those noted above.
Nexus IT is in our 20th year of business. We have an intensive focus on cybersecurity defense, compliance and remediation for SMBs.
The Following Are Some Key Concepts You Should Understand
Hacker (Black Hat Hacker): A black hat hacker is a person who looks for computer security vulnerabilities and exploits them for personal financial gain or other malicious reasons. This differs from white hat hackers who are security specialists that are employed to find security flaws that black hat hackers may exploit.
The Dark Web: This is an underground internet where criminals operate. They can buy ransomware kits on the Dark Web that come along with support services and everything they need to set up a business for only $2,500. The Dark Web requires specific software, configurations or authorization to access.
Attack Vector: This is where hackers gain unauthorized access to a device or a network for nefarious purposes. Attack vectors help hackers exploit the vulnerabilities in your system or network, including your employees.
Ransomware: This is a malware virus that infects, locks or takes control of a system and then demands a ransom to reverse it. The hacker encrypts your data and scrambles it so you can’t access it. Ransomware attacks and infects your computer with the intention to extort money from you. It’s installed via a malicious email attachment, an infected software download, and/or when you visit a malicious website or link.
Phishing: Phishing websites lure email recipients and Web users into believing that a spoofed website is legitimate. The hacker’s goal is to acquire private data, such as credit card numbers, personal information, account usernames, and passwords. The phishing victim then discovers his personal identity and other vital information was stolen and exposed.
Spear Phishing: This is a variation on phishing where hackers send emails to groups of people with common characteristics or other identifiers. The spear phishing email appears to come from a trusted source but in reality, helps hackers obtain classified information. The email may pretend to be from your boss or CEO, or a large financial institution.
Worm: This is a type of malicious software (malware) that worms its way through your network. It infects your computer and replicates across other computers, leaving copies of itself in the memory of each it infects. Worms often originate from e-mail attachments that appear to be from trusted senders. Then they spread to your contacts via your e-mail account and address book.
Who’s Attacking You?
Organized Crime 80% of hackers are affiliated with organized crime. Hacking is a lucrative business for criminals. Some of these “mafias” contain 5,000+ criminals. They use multiple computers at a time, and sophisticated software to try to hack into your systems.
Nation States (Russia, North Korea, China, etc.) Nation-state hackers target government institutions, industrial facilities and businesses to interrupt operations and leak confidential information. Hacking can result in massive data and revenue loss.
Hacktivists (Anonymous and Shadow Brokers) Hacktivism is the act of hacking or breaking into a computer system for a politically or socially motivated purpose. They organize on the deep/dark web to set up attacks.
Lone Wolves (Intelligent, Financially Driven, Unscrupulous) The majority of people hacking are just individuals who aren’t connected to a hacking network other than chat rooms and online forums.
Malicious Insiders (Disgruntled Employees or Contractors) This is an insider with authorized system access. They have an advantage over external attackers because they have the authority to access your IT and are probably familiar with your network architecture and system policies/procedures. Most organizations focus on external threats and don’t adequately protect their confidential data from insiders.
Attack Vectors You Should Watch For
Physical: (Theft, malicious USB drives, unsecured workstations) Hackers with physical access to servers may extract sensitive data while it’s in use and bypass traditional in-transit and at-rest controls. They can also simply remove a memory card from the server and read its contents on another computer.
Endpoints: (Remote attacks on vulnerable workstations) Hackers get into computers by convincing employees to click on malicious e-mail attachments, web links, and drive-by downloads.
Mobile Devices: Exploitation of iOS and Android systems. Bluetooth is one of the main security gaps by which hackers get into your phone. This is growing in prevalence.
The Cloud: Cloud services like Azure and AWS have become mission-critical for many organizations. Organizations administrative credentials for cloud services are of high value to hackers. Attacking an organization’s cloud administrator’s account and leveraging those credentials can lead to greater data exfiltration. This can put your entire organization at risk.
IoT: The Internet of Things devices such as security cameras connected to the Internet are vulnerable to hackers. IoT hacking has been extremely successful, resulting in Distributed Denial of Service attacks that cripple infrastructures, systems, and business operations.
Human Attack Vectors: Humans are involved in nearly 98% of all attacks. Negligent employees are the number-one cause of data breaches in small and medium-sized businesses. Careless workers and poor passwords have led to a rise in ransomware attacks and other breaches on small businesses, which cost an average of $1 million.
Washington State University was sued for a data breach that affected 1 million individuals and for not notifying them in accordance with regulations. A hard drive was stolen containing data from one million individuals. This data was collected by school districts tracking students after graduation to see if they went to college or got jobs. The theft occurred in April 2017, but university officials didn’t disclose it until June 9, 2017.
Malicious Emails
Email is the easiest method of delivery for malicious payloads. Hackers who use this approach cast a very wide net. Humans are involved in almost all malicious email initiations. Learning to identify fraudulent email is essential for every employee, technical or not.
Examples Of Real Phishing Emails
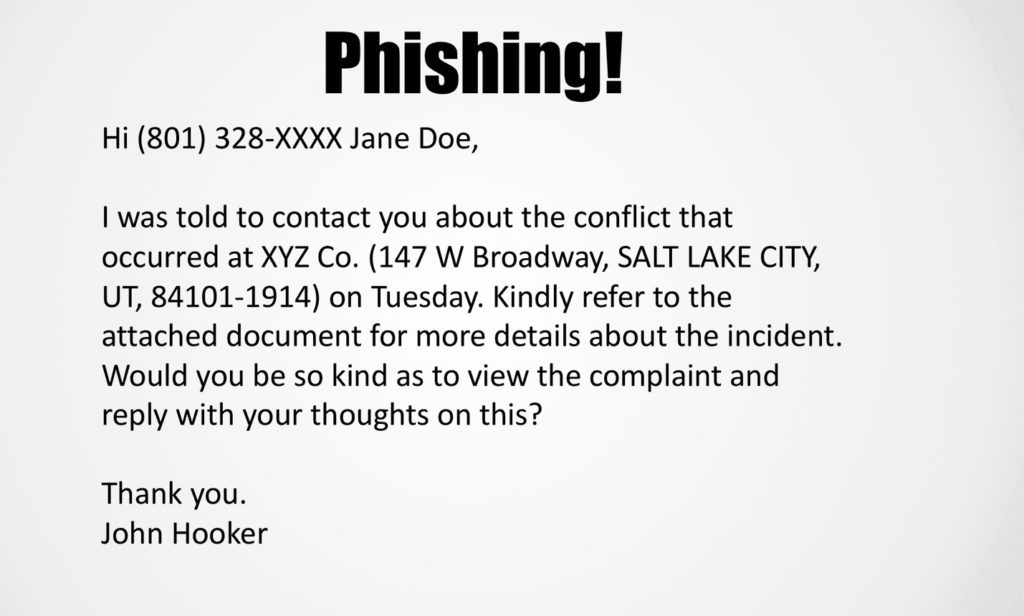


Common Themes To Look For In A Malicious Email
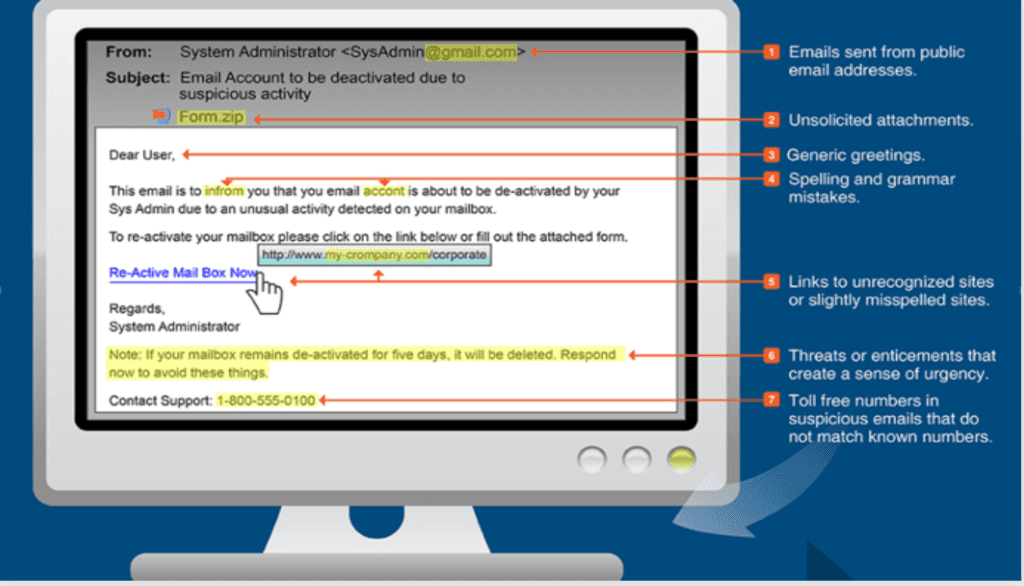
Watch Out for Spoofed URLs
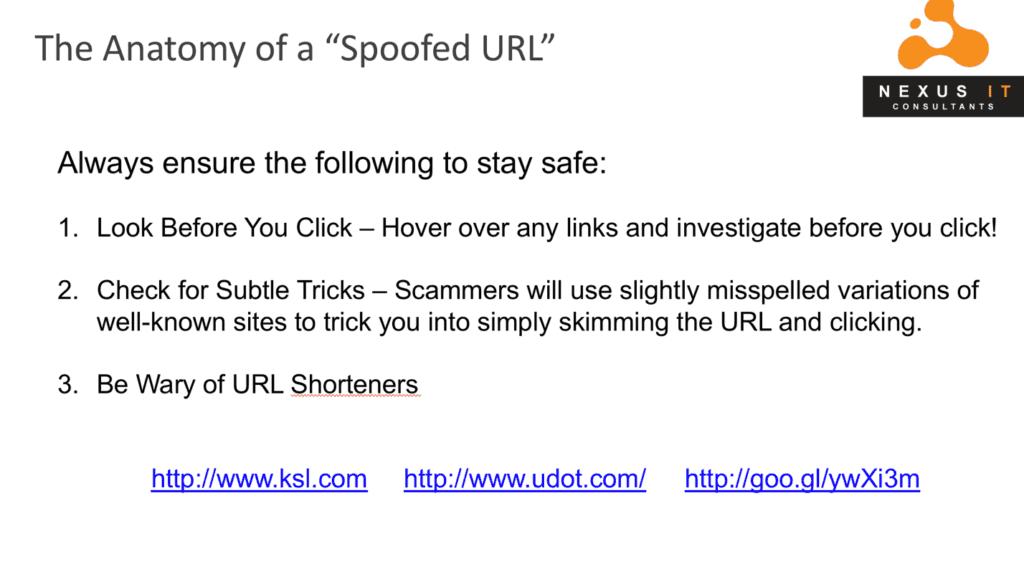
Always ensure the following to stay safe:
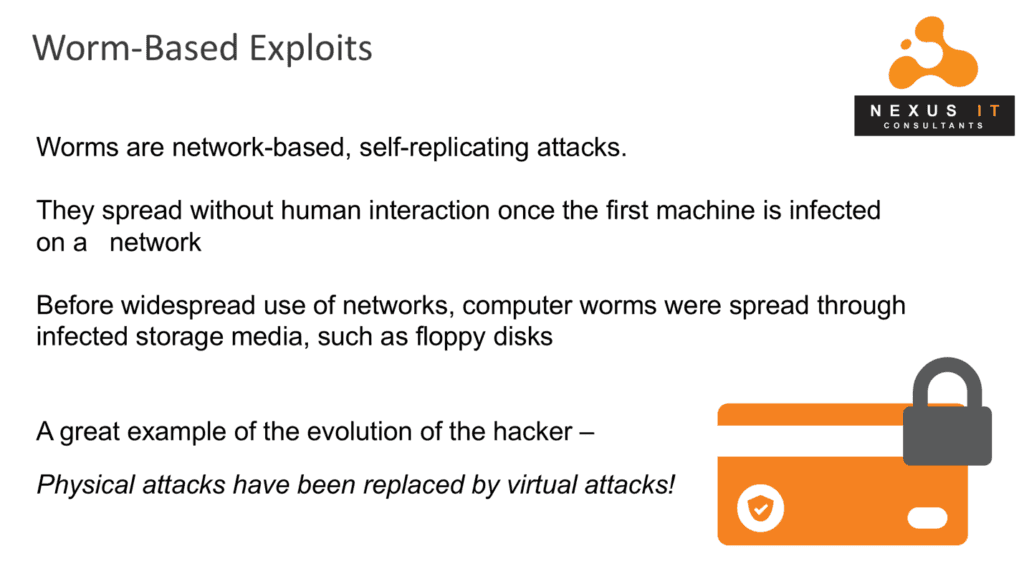
Beware of Worm-Based Exploits
These are self-replicating attacks that spread without human interaction once the first machine is infected on a network. Before the widespread use of networks, computer worms were spread through infected storage media like floppy disks. Today these physical attacks are replaced by virtual ones!
The good news is that worms often use legacy vulnerabilities and can be remedied with active patching and proper endpoint protection. It’s much easier to have your IT provider patch your healthy IT system than it is to bring them in for a messy cleanup!

WannaCry—The Ransomware That Came With A Worm
WannaCry encrypted files like ransomware by changing the extensions to wnry, .wcry, .wncry and .wncrypt. The ransomware then spread rapidly, like a worm, exploiting a Windows vulnerability in the Windows Server Message Block (SMB) service which Windows computers use to share files and printers across local networks.


What To Do If You Experience An Infection Or Breach
Always Follow These Best Practices
The GDPR
General Data Protection Regulation
The GDPR affects all internet business worldwide. It’s a very complex law, so we can’t explain everything here. We’ve provided some resources below that you should check out. Keep in mind that there are many gray areas where this law is concerned. So, you should do some research to determine how the law affects your organization’s unique situation.
The GDPR is an internet privacy law. All businesses, small or large, and even entrepreneurs who do business on the Internet with consumers who are European Union citizens need to be aware of how the law affects them.

It doesn’t matter if your company is inside the EU, or anywhere else in the world– If you do business with anyone who is a citizen of the following countries, you must have complied with this new law by May 25, 2018:

The GDPR is a consumer data protection law. It ensures that individuals can:
The GDPR applies to the acquisition, processing, and storage of personal data – from initial gathering to final deletion of this data and every point in between. It applies specifically to personal data and anything that pertains to identifiable data such as:
This could be information you collect automatically from Google, an opt-in, or other collection methods online – anything that would identify an individual.

What Should You Do?
There are three requirements you must meet:
1. Controls and Notifications
2. Transparent Policies
3. IT and Training
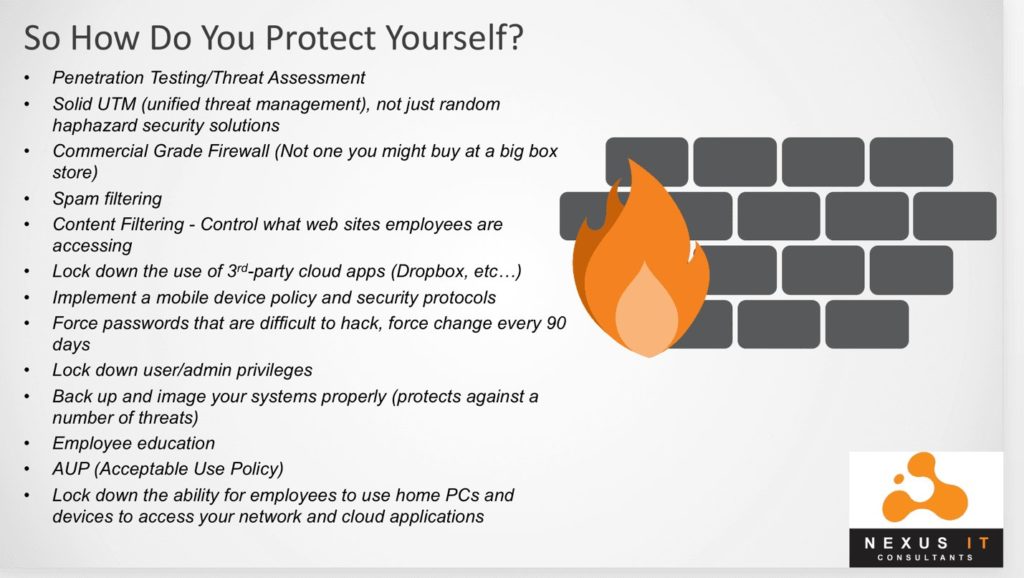
How Do You Protect Yourself?

Protect Your Business In Utah – Contact Nexus IT Consultants


For more information about hackers, today’s exploits and cybersecurity for your business, call the experts at Nexus IT Consultants in Park City, Salt Lake City or Provo Utah at or (435) 659-2533, or send an email to .